Active Directory // Domain Controller Setup with Windows 10 Client

The Goal
My goal with this lab is to create a Windows Server 2019 VM to act as a Domain Controller for an Active Directory environment and then I want to create a Windows 10 Pro VM to act as a client on the domain.
This article from Let’s Learn IT helped a lot with visually laying out the network topology and walking through the process.

Server Setup
First step is to create a new VM using the Windows Server 2019 Evaluation ISO and get it up and running in Virtual Box.
I ended up giving the server 4GB of RAM and 4 cores. Based on the network topology, this server needs two network interfaces; one in the default NAT mode to reach the internet through my host machine and one on an internal network that the AD domain will be on.
Now that the Windows Server is up and running, I need to open Server Manager to add Active Directory Domain Services.
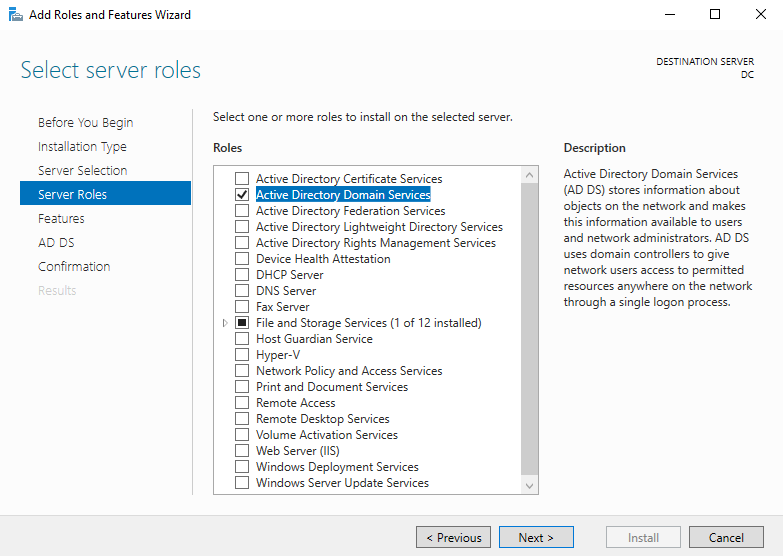
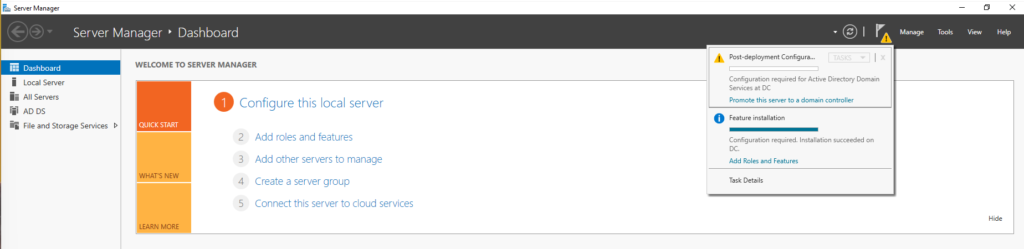
With that installed, I can promote this machine to Domain Controller.
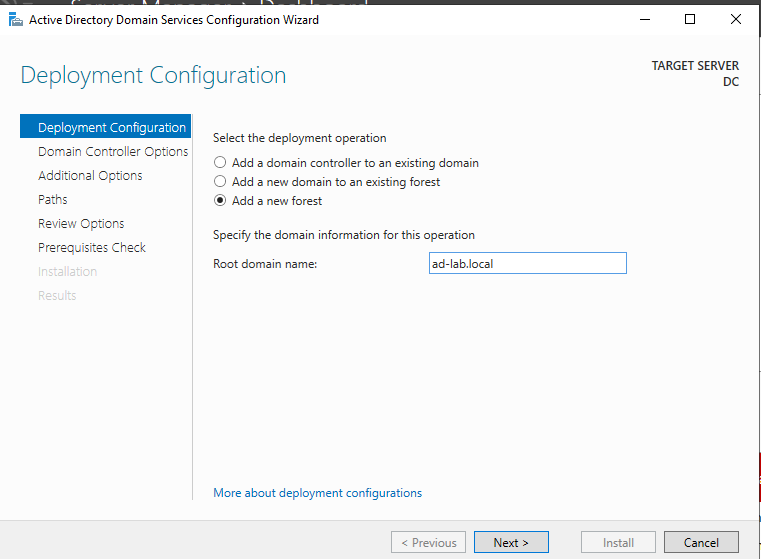
In the configuration I’ll choose to add a new forest and name it ad-lab.local.
Now I’ll create a dedicated Domain Admin account instead of using the default Administrator account. I do this in Active Directory Users and Computers.
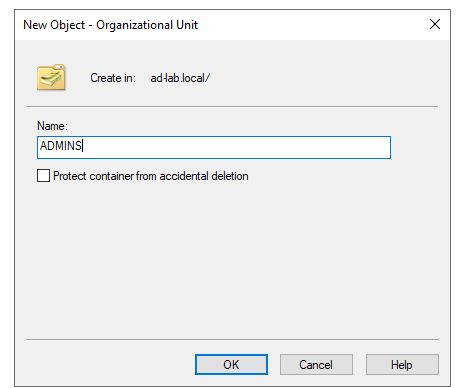
I’ve chosen to add a new OU named ADMINS to keep things clean.
In the new OU I created a new User and added my info.
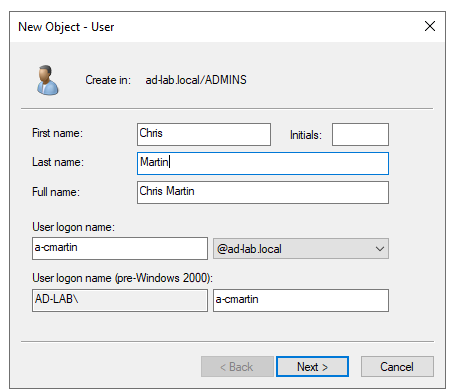
Then I made my new account a member of the Domain Admins group.
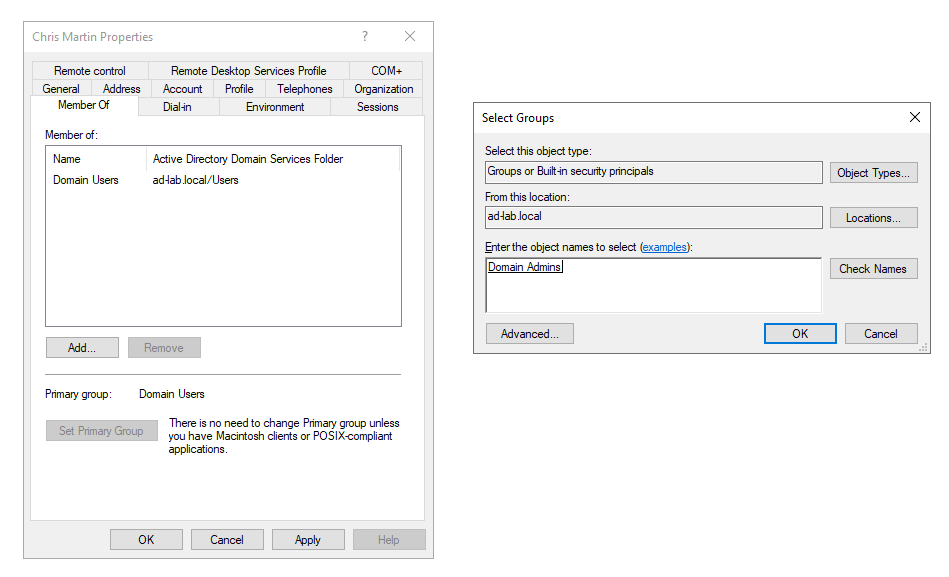
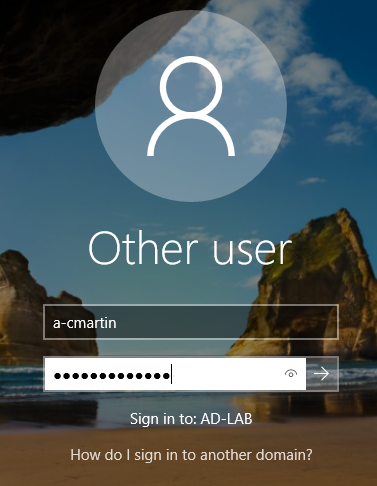
Now I can sign in to this new account, just for me, and I’ll still have Admin permissions.
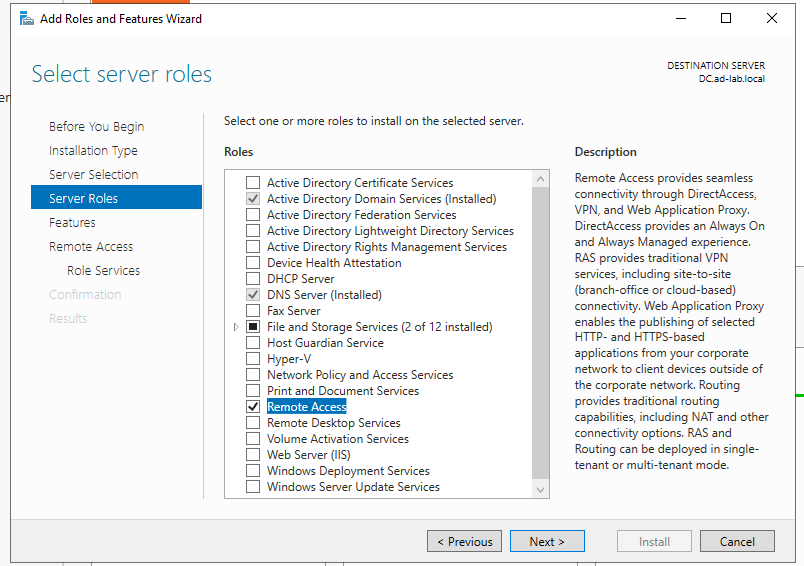
The next server role I need to add according to the topology is Remote Access.
With that installed, I can now set up NAT so that clients can send internet traffic requests through the Domain Controller.
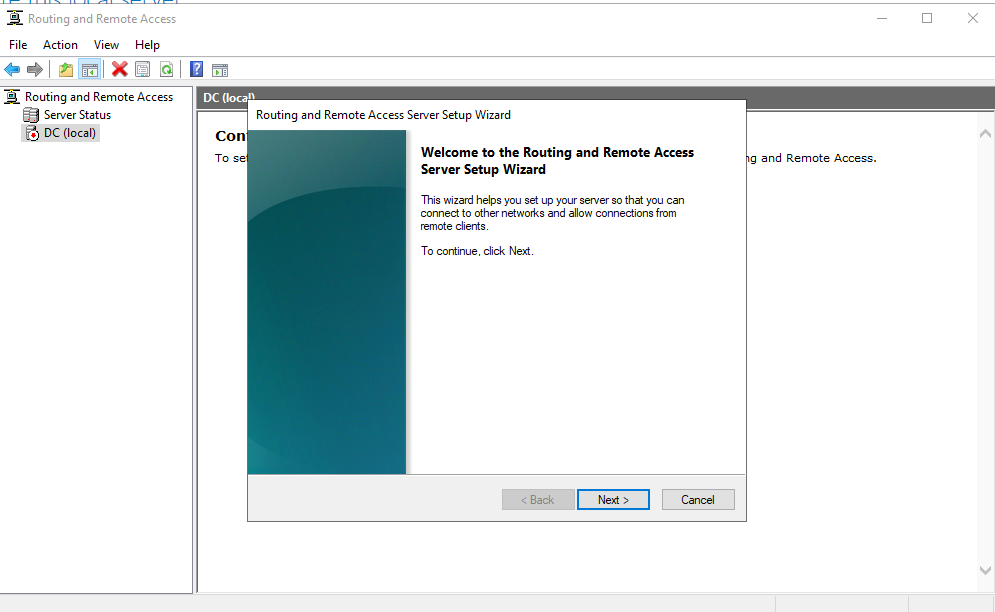
Under the Routing and Remote Access tool I right click the DC and click configure and enable routing and remote access, configure as NAT, and choose the correct network interface that’s connected to my home internet.
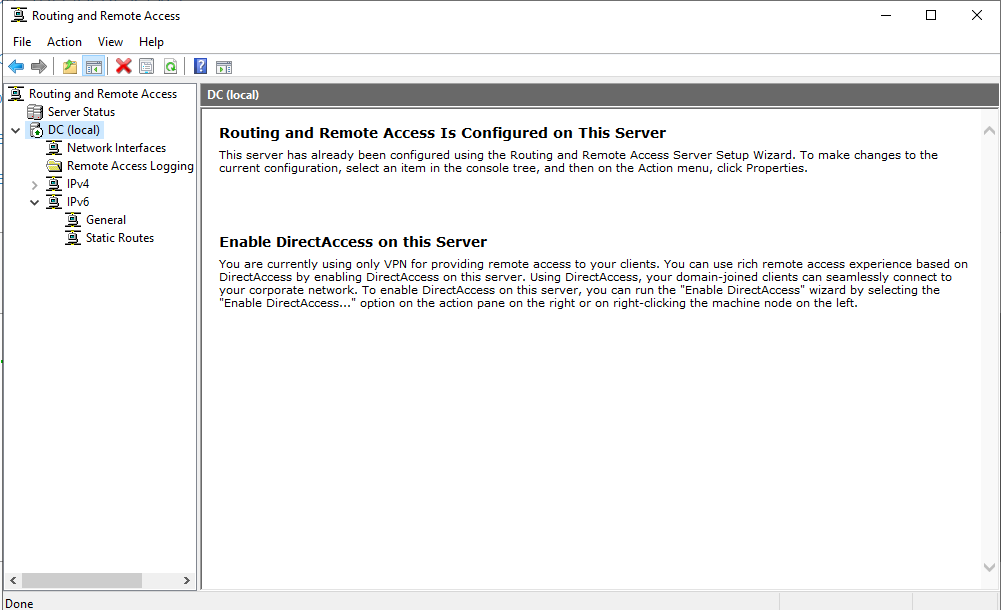
The last step to setting up the server is to add and configure DHCP so clients that connect to the network receive an IP address from the DC.
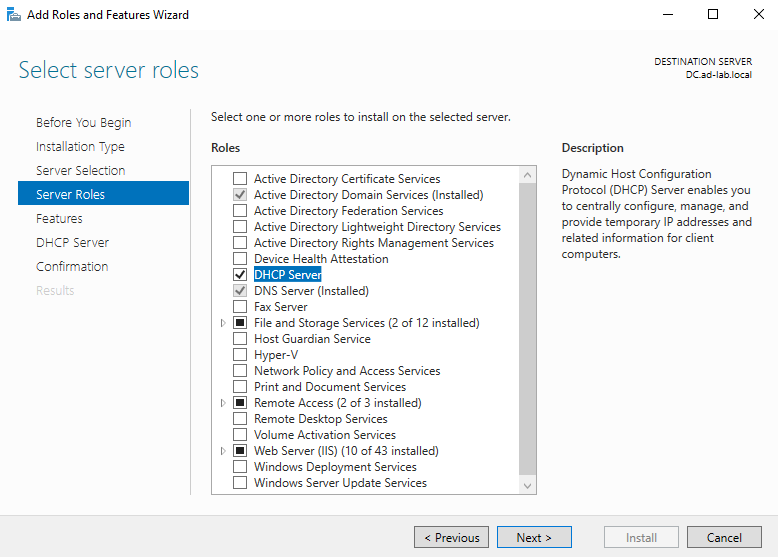
With the DHCP role added I can define a new scope under the DHCP tool.
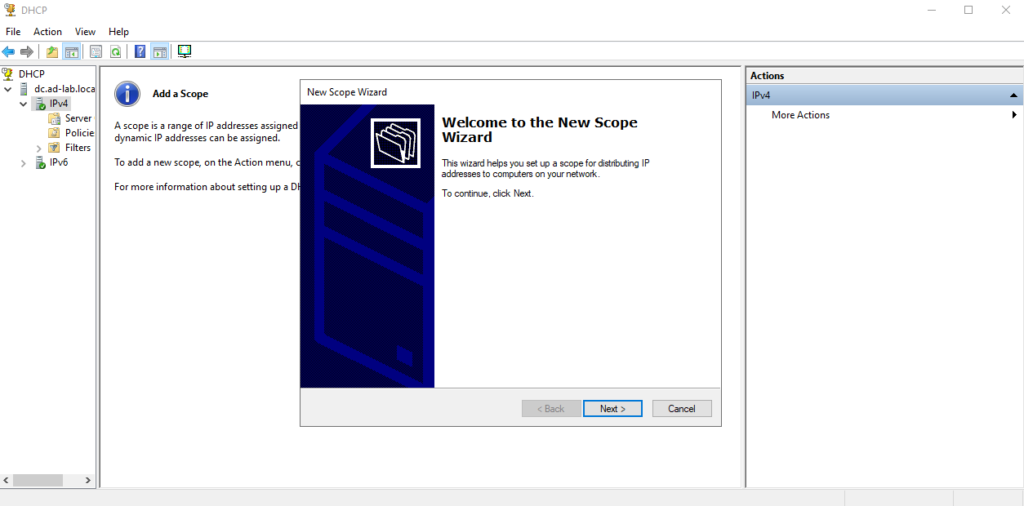
Here I define the IP Range for DHCP, set the default gateway as the network interface that’s on the internal network, and set the loopback address as the DNS server (since DNS is installed on the DC when Active Directory is installed).
If I now right-click the domain and Authorize then Refresh, the IPv4 scope has a green check.
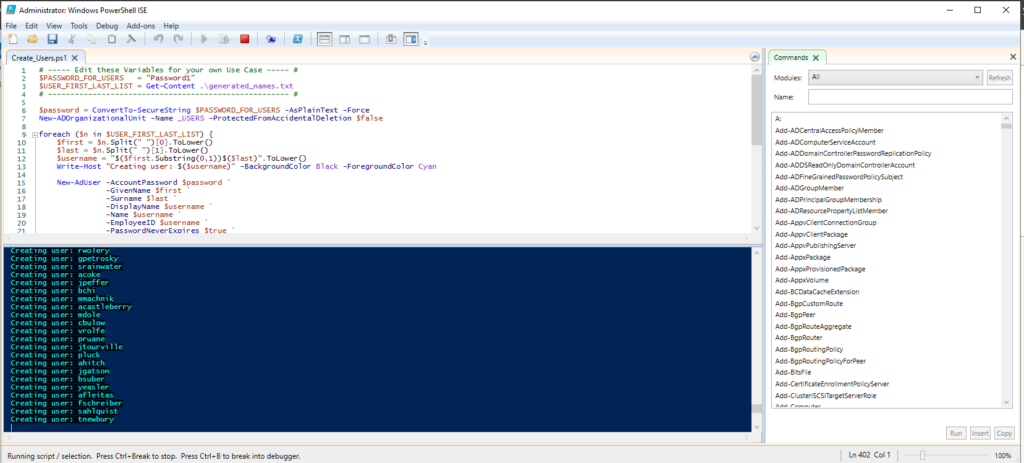
Generating 1,000 Users with PowerShell
In order to not have an empty Active Directory, the walkthrough provided a PowerShell script that creates 1,000 users and adds them to a new OU, _USERS. It creates usernames in the scheme: (First Initial)(Last Name) and auto assigns them all the password: Password1
I also added my own name to the list of random names so that I’ll have a normal Domain User account as well as a Domain Admin one.
Adding Windows 10 Client to Domain
Next I created a Windows 10 Pro VM and changed it’s network interface to be on the same internal network as the second interface on the Domain Controller.
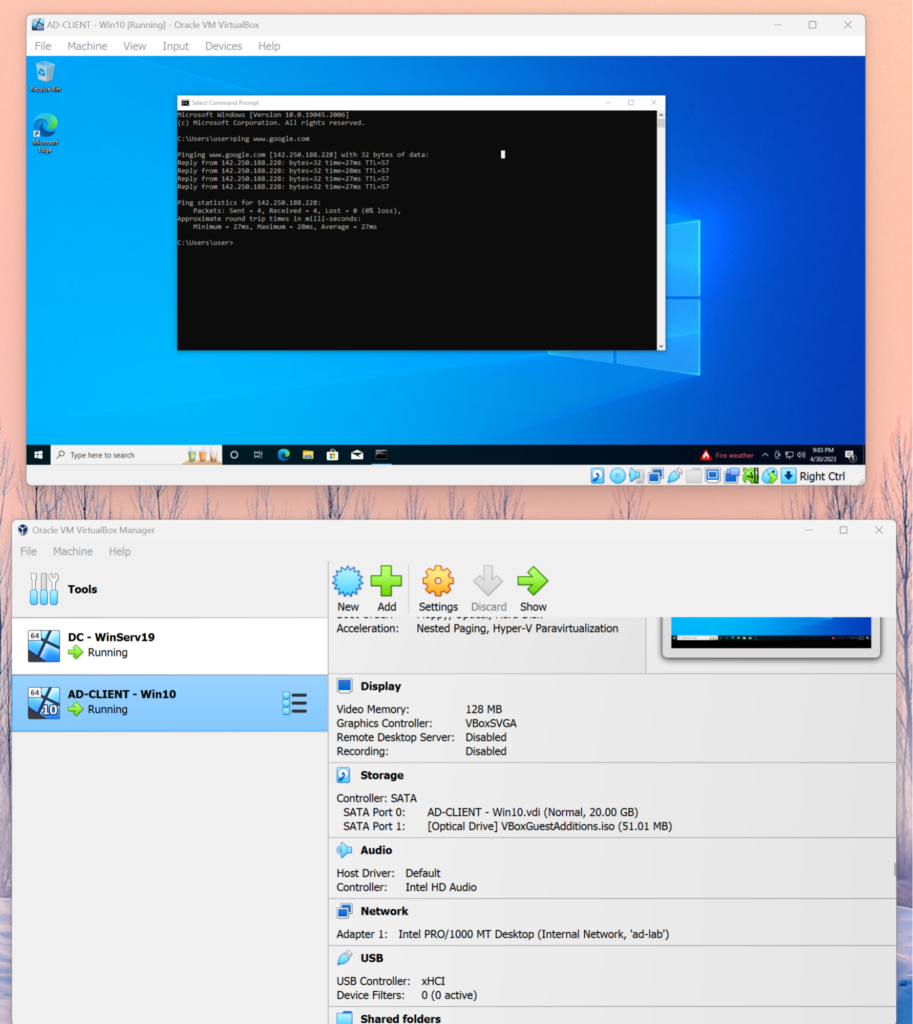
I verify that the DC networking is correct by pinging google from the client machine. Even though the client machine is on an internal network, when it joined that network the DHCP Server on the DC assigned it an IP from the range I set, and the NAT allows me to send the requests from the client through the DC and out to the internet on the first network interface.
In order to connect the client to the domain, I open settings and choose Rename this PC (advanced) and choose the button Change…
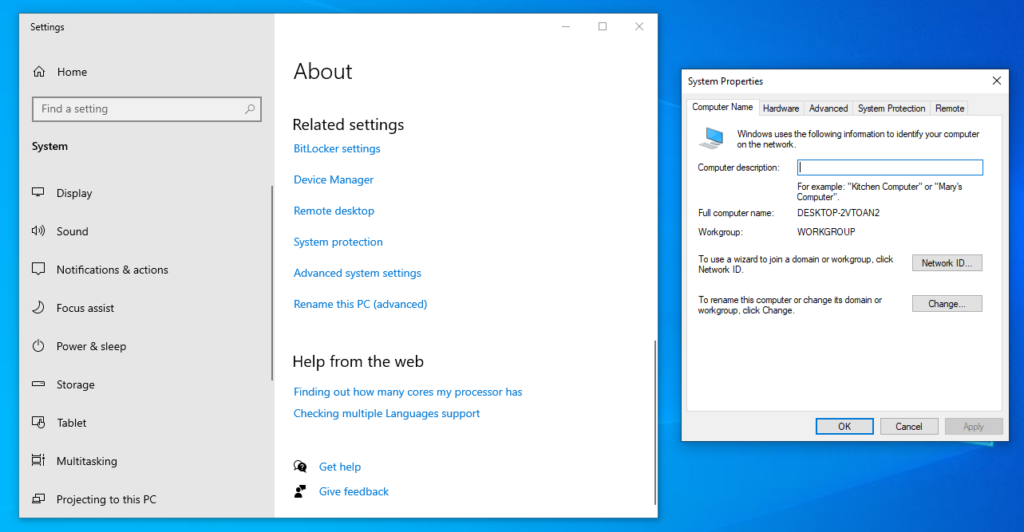
I renamed it to CLIENT01 and made it a member of the ad-lab.local domain. This prompts to log in with credentials with proper permissions.
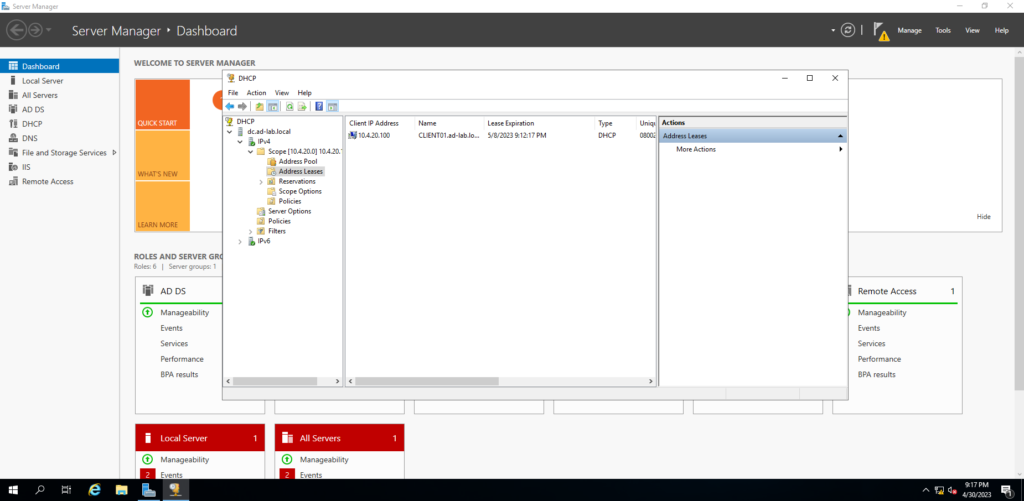
Back on the DC, if I open Server Manager and the DHCP tool, I can see CLIENT01 now listed under Leases.
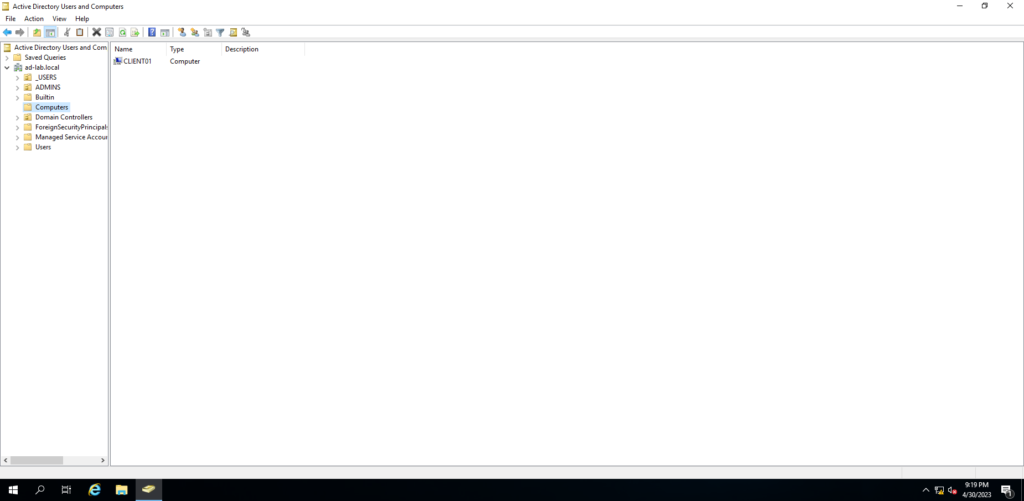
It also shows up under Active Directory Users and Computers, in the computers folder.
Verification
Everything should be setup now. The Windows Server is running an Active Directory Server, a DNS Server, and a DHCP Server. The Windows 10 Pro VM has been added to the domain and can successfully send internet requests through the DC to the internet.
Now I can log in to a couple of different accounts on the Windows 10 VM to make sure they can all get in.
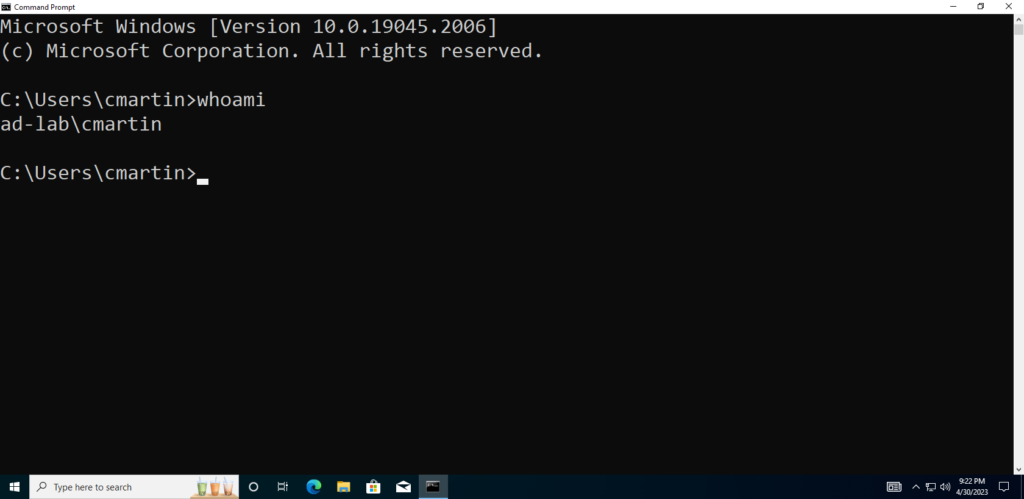
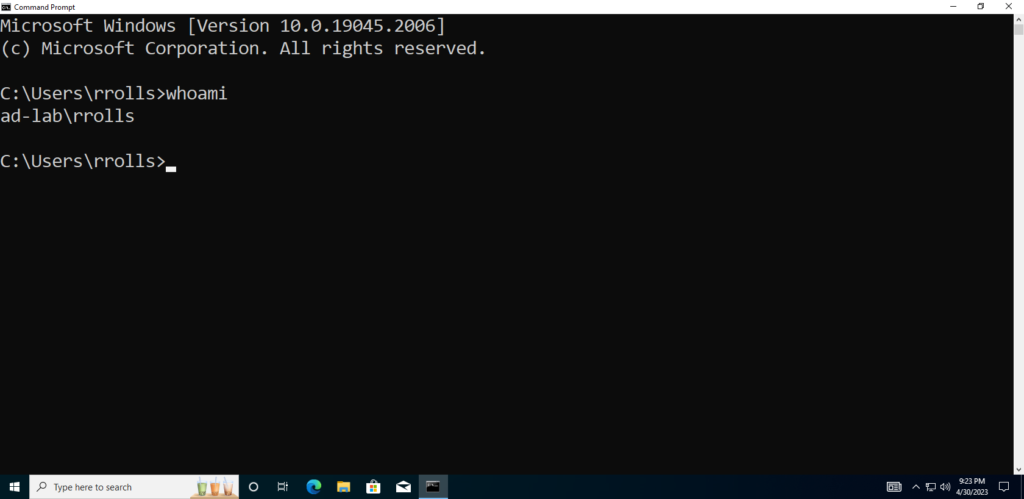
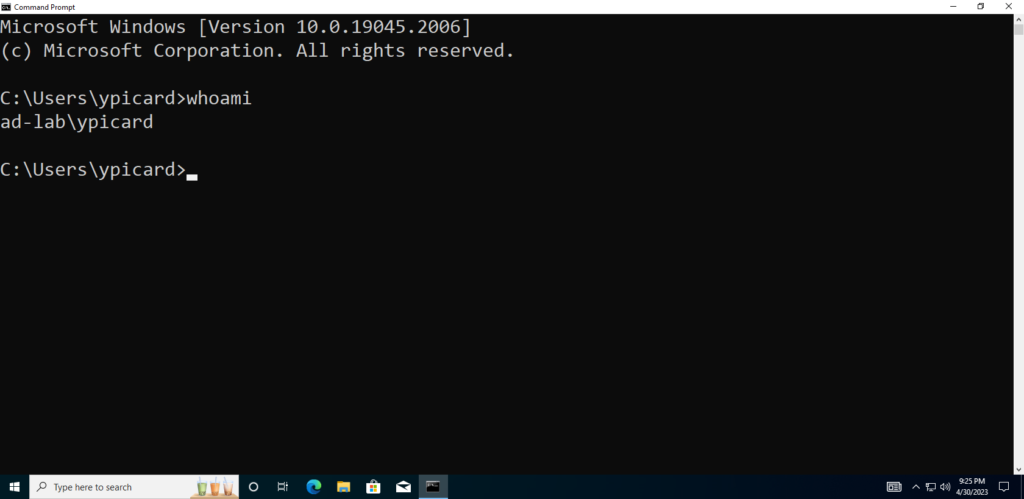
Success!
I had a lot of fun setting all of this up and I learned quite a bit about Active Directory & Networking. I’m looking forward to playing around with Active Directory more, especially with managing and configuring Group Policies, enabling & disabling permissions, and more.